4-6
C7200 VSA (VPN Services Adapter) Installation and Configuration Guide
OL-9129-02
Chapter 4 Configuring the VSA
Configuration Tasks
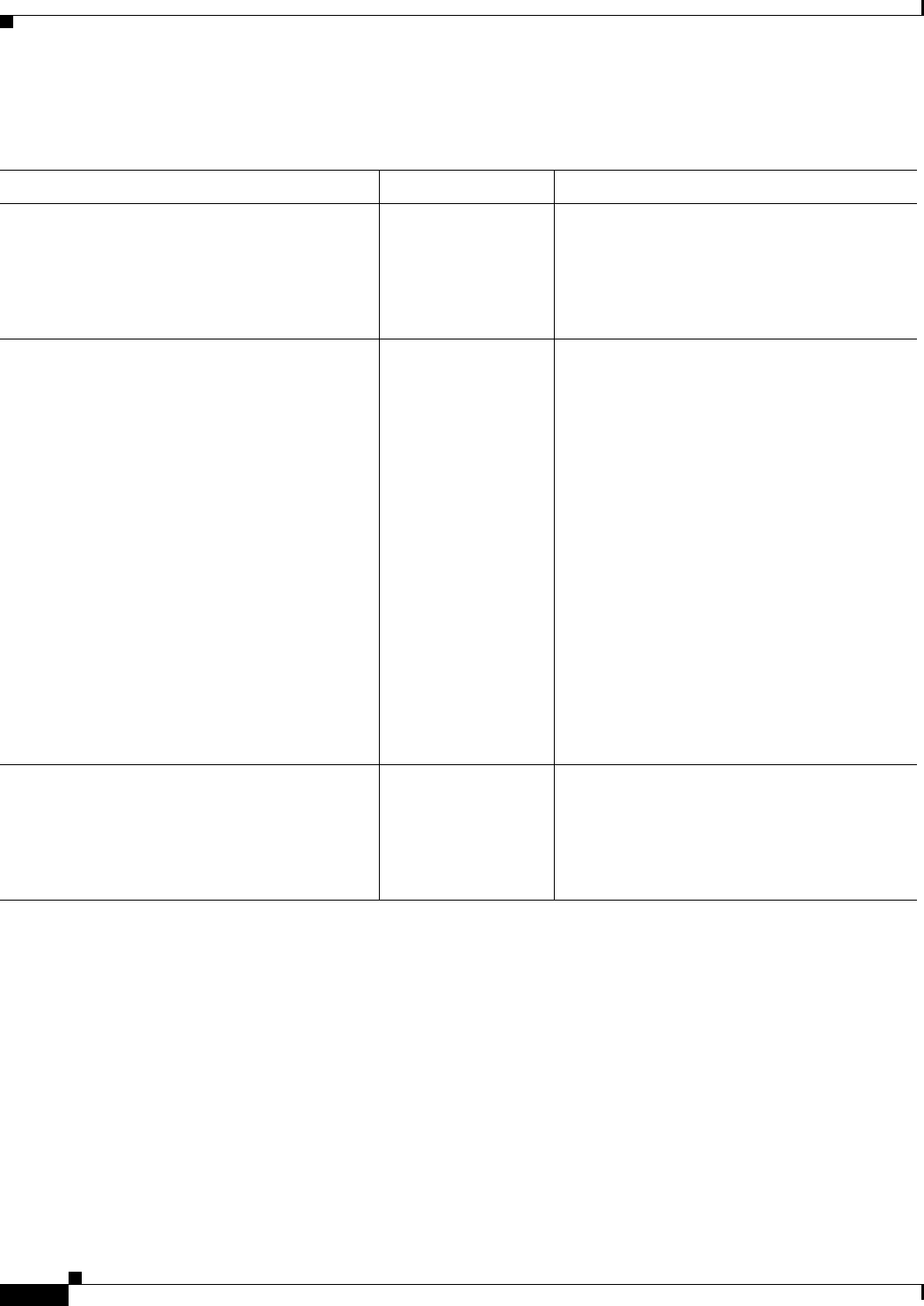
Table 4-1shows allowed transform combinations for the AH and ESP protocols.
Examples of acceptable transform combinations are as follows:
• ah-md5-hmac
• esp-des
• esp-3des and esp-md5-hmac
• ah-sha-hmac and esp-des and esp-sha-hmac
The parser will prevent you from entering invalid combinations; for example, once you specify an AH
transform it will not allow you to specify another AH transform for the current transform set.
Table 4-1 Allowed Transform Combinations
Transform type Transform Description
AH Transform (Pick up to one.) ah-md5-hmac
ah-sha-hmac
AH with the MD5 (Message Digest 5)
(HMAC variant) authentication algorithm
AH with the SHA (Secure Hash Algorithm)
(HMAC variant) authentication algorithm
ESP Encryption Transform (Note: If an ESP
Authentication Transform is used, you must
pick one.)
esp-aes
esp-aes 128
esp-aes 192
esp-aes 256
esp-des
esp-3des
esp-null
ESP with the 128-bit Advanced Encryption
Standard (AES) encryption algorithm
ESP with the 128-bit AES encryption algorithm
ESP with the 192-bit AES encryption algorithm
ESP with the 256-bit AES encryption algorithm
ESP with the 56-bit Data Encryption Standard
(DES) encryption algorithm
ESP with the 168-bit DES encryption algorithm
(3DES or Triple DES)
Null encryption algorithm
ESP Authentication Transform (Pick up to
one.)
esp-md5-hmac
esp-sha-hmac
ESP with the MD5 (HMAC variant)
authentication algorithm
ESP with the SHA (HMAC variant)
authentication algorithm
